Last Updated on January 8, 2026
Introduction: The Internet Has a Side You Never See
When most people think of search engines, they think of websites, articles, videos, and images. But the internet isn’t just made up of web pages. It’s filled with servers, webcams, routers, industrial systems, databases, and smart devices quietly connected and often exposed.
The Shodan search engine exists to index that side of the internet.
For cybersecurity professionals, Shodan isn’t a curiosity or a hacking tool. It’s a visibility platform that reveals how exposed systems really are. Used responsibly, it helps organizations identify risk, monitor attack surfaces, and understand global security trends.
This article explains how the Shodan search engine is used in cybersecurity, what it reveals, and why it has become an essential tool for defenders rather than attackers.
What Is the Shodan Search Engine?
Shodan is a specialized search engine that indexes internet-connected devices instead of websites.
Rather than crawling web pages, Shodan scans:
- IP addresses
- Open ports
- Network services
- Banners and metadata
It collects publicly available information about devices that are accessible from the internet.
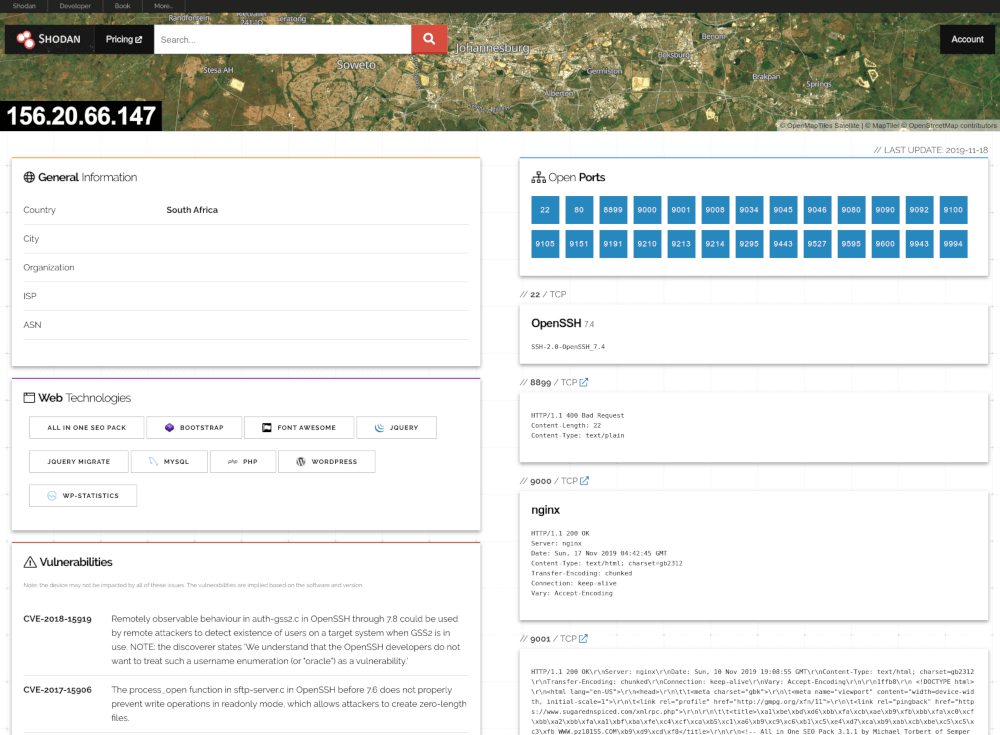
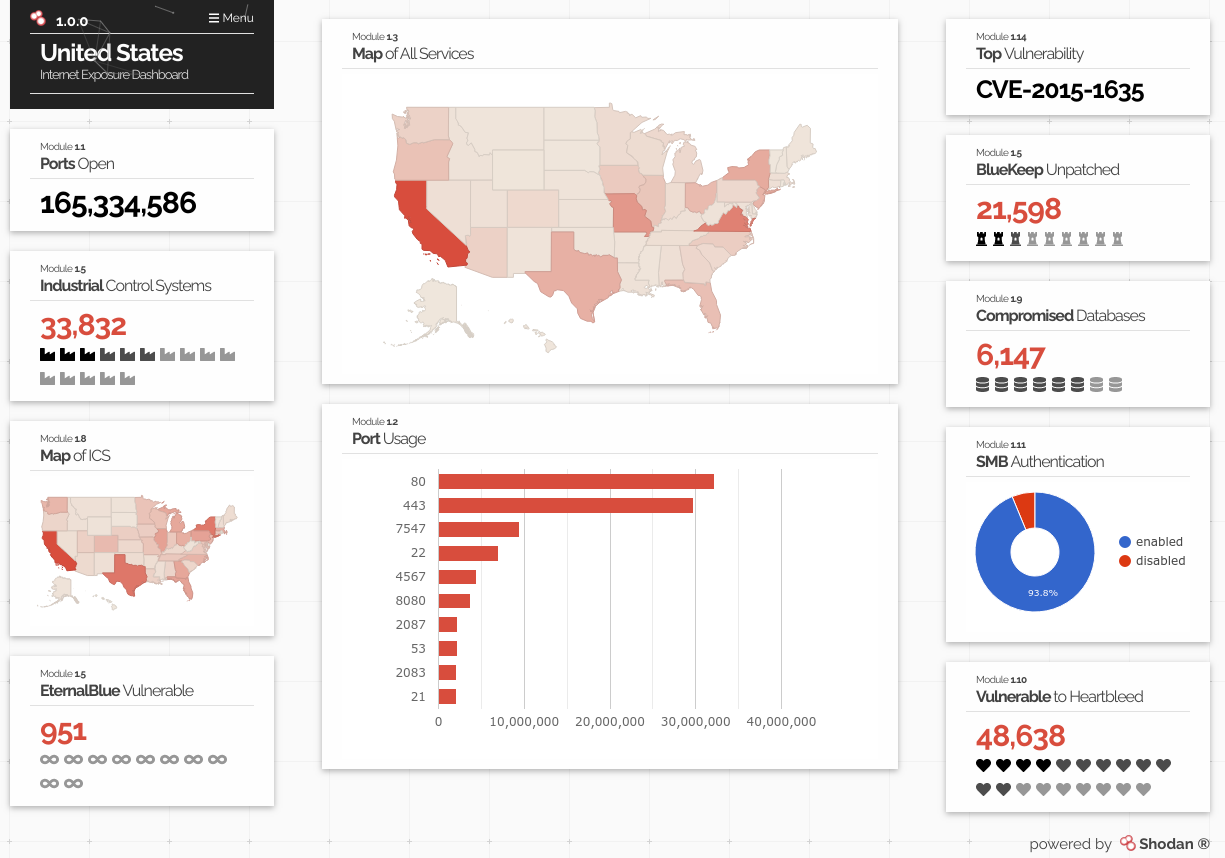
The key distinction is this: Shodan does not break into systems. It shows what systems are already exposing.
Why Shodan Matters in Cybersecurity
Cybersecurity is fundamentally about visibility. You can’t protect what you don’t know exists.
Many breaches happen not because of sophisticated attacks, but because:
- A system was accidentally left exposed
- A service was misconfigured
- Default settings were never changed
- An old system was forgotten
Shodan helps security teams see what attackers can already see.
Core Ways the Shodan Search Engine Is Used in Cybersecurity
Identifying Exposed Systems
One of Shodan’s primary cybersecurity uses is exposure discovery.
Security teams use it to:
- Find publicly accessible servers
- Detect exposed databases
- Identify internet-facing devices
- Locate systems that should not be public


This is especially important for large organizations with complex infrastructure.
Attack Surface Management
Modern organizations don’t have a single perimeter. They have an attack surface that constantly changes.
Shodan helps teams:
- Understand what assets are internet-facing
- Monitor changes over time
- Detect newly exposed services
- Validate asset inventories
In cybersecurity, unmanaged assets are often the weakest link.
Vulnerability Awareness and Risk Prioritization
Shodan provides contextual data about:
- Software versions
- Service banners
- Encryption usage
- Known insecure configurations
This allows security teams to:
- Identify potentially vulnerable systems
- Prioritize remediation
- Focus on high-risk exposures
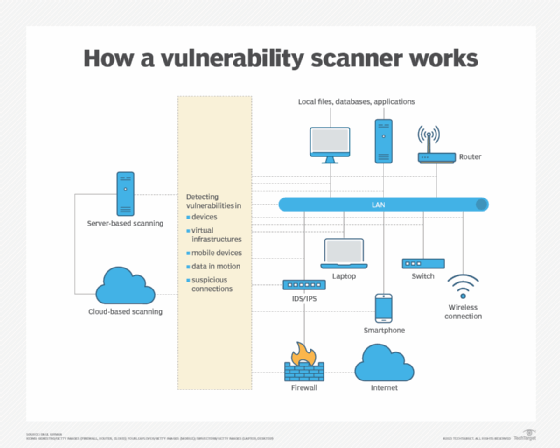

Importantly, this supports defensive decision-making, not exploitation.
Incident Response and Threat Investigation
During a security incident, time matters.
Shodan can help responders:
- Determine whether similar systems are exposed elsewhere
- Assess whether an issue is isolated or systemic
- Understand how widely a vulnerability may be visible
This broader context improves response quality and speed.
Monitoring for Policy Violations
Many organizations have strict rules about what can be internet-facing.
Shodan is used to:
- Validate compliance with security policies
- Detect unauthorized exposure
- Identify shadow IT systems
- Confirm remediation efforts worked
It acts as an independent external check.
Shodan in Red Team and Blue Team Work
Shodan is used across defensive disciplines.
Blue Team (Defensive Security)
Blue teams use Shodan to:
- Audit external exposure
- Improve security posture
- Reduce attack surface
- Support continuous monitoring
The focus is prevention and awareness.
Red Team (Authorized Testing)
In controlled, authorized environments, red teams may use Shodan to:
- Simulate attacker reconnaissance
- Demonstrate real-world visibility
- Educate stakeholders on risk
This use is ethical and permission-based, not opportunistic.
Common Cybersecurity Use Cases by Sector
Enterprise IT
Enterprises use Shodan to:
- Track externally exposed services
- Validate cloud security configurations
- Monitor mergers and acquisitions risk
- Reduce unknown assets
Healthcare and Critical Infrastructure
Sensitive sectors use Shodan to:
- Identify exposed medical devices
- Monitor industrial control systems
- Reduce regulatory risk
- Protect patient and operational safety


Visibility here can prevent serious real-world consequences.
Government and Public Sector
Public agencies use Shodan to:
- Assess national exposure trends
- Support risk assessments
- Improve infrastructure security
- Inform policy and standards
Is Shodan Itself a Security Risk?
This question comes up frequently.
Shodan does not:
- Hack systems
- Bypass authentication
- Exploit vulnerabilities
- Create exposure
It reveals what is already publicly accessible.
The real risk is misconfiguration, not Shodan.
If Shodan can see a system, so can anyone else.
Ethical and Legal Use in Cybersecurity
Shodan is legal to use in most jurisdictions because it:
- Collects publicly available information
- Does not require credentials
- Does not access protected data
However, ethical use requires:
- Authorization for testing
- Responsible disclosure
- Clear defensive intent
Professional cybersecurity teams operate within these boundaries.
Misconceptions About Shodan in Cybersecurity
“Shodan is a hacking tool.”
It’s a visibility and reconnaissance tool.
“Only attackers use Shodan.”
Defenders use it extensively.
“If it’s on Shodan, it’s compromised.”
Exposure does not equal breach.
“Blocking Shodan fixes the problem.”
Fixing configuration does.
Understanding these points reduces fear and misuse.
How Shodan Complements Other Security Tools
Shodan is not a replacement for:
- Vulnerability scanners
- Firewalls
- SIEM platforms
- Endpoint protection
Instead, it complements them by providing external perspective.
Internal tools show what you think you have.
Shodan shows what the internet can actually see.
That difference is powerful.
Why Cybersecurity Professionals Value Shodan
Shodan helps answer critical questions:
- What is exposed right now?
- What changed recently?
- How visible are we to attackers?
- Where should we focus first?
In a field where blind spots are costly, that insight is invaluable.
The Bigger Lesson: Security Starts With Visibility
Shodan highlights a core cybersecurity truth: many risks are self-inflicted through misconfiguration and neglect, not advanced attacks.
Organizations that use Shodan responsibly tend to:
- Discover issues earlier
- Reduce external exposure
- Improve security maturity
- Make better prioritization decisions
Conclusion: A Defensive Tool for an Exposed Internet
The Shodan search engine is not about breaking into systems. It’s about understanding how exposed systems already are.
In cybersecurity, Shodan is used to:
- Identify risk
- Manage attack surfaces
- Support incident response
- Improve accountability
Used ethically and responsibly, it helps defenders think like attackers without becoming one.
If your organization is evaluating external exposure, cybersecurity monitoring, or risk management strategies, fill out our contact form or reach out to us today. Visibility is the first step toward security.
